Delivery Accuracy
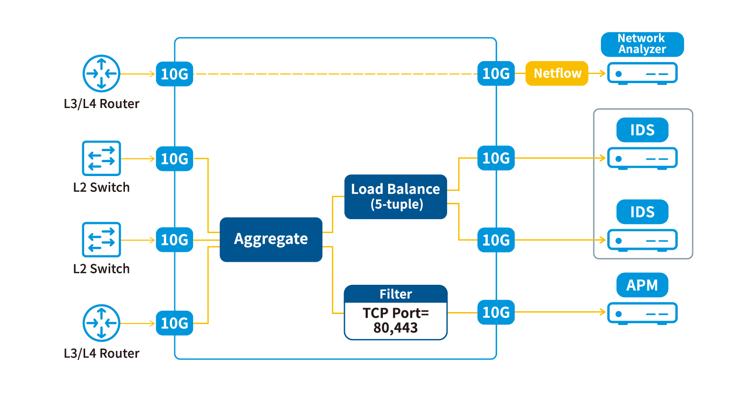
GRISM aggregates several inputs and accurately delivers the packets by not only L2-L4 filtering but also the application-aware pattern-based filtering above L4 : filter HTTP connection packets by HTTP URL, filter SIP messages by SIP URI, filter DNS by domain and so on.
GRISM’s Fair-Distribution mechanism satisfies every analysis device by properly duplicating the packet that belongs to the demand intersection for multiple analysis devices.
Filtered traffic can be distributed to a group of egress ports with session-based balancing strategy to guarantee “same session to the same destination”. When one egress port is disconnected, GRISM failovers the stream to the stand-by port or redistribute to the other ports in the group.
Tunnel Handling and Packet Reengineering
The filtering functions can automatically apply on the tunnel payload if plain Ethernet packets and tunnel packets are mixed in the input traffic. Since most analysis devices can only handle plain packets well, GRISM is able to do tag-removal or re-capsulation.
Moreover, slicing packet payload is supported for analysis offload such as removing TCP/UDP payload for the device that works on L2-L4 header only.
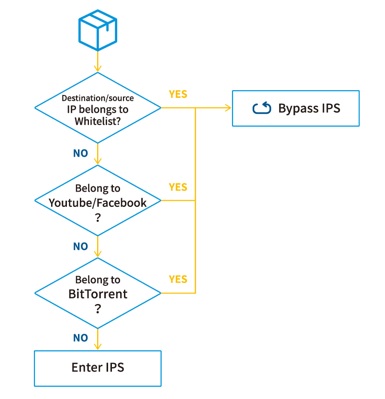
Intelligent Content-based Bypass
GRISM supports Intelligent Bypass function to protect production network when in-line analysis devices are deployed. It detects the status of in-line device and immediately enable bypass when that device gets problems. The uniqueness of GRISM is to bypass the traffic which is not the packet of interest or with little risk. For example, the enterprise deploys IPS guarded by GRISM to avoid YouTube from entering IPS.
Netflow Generation
Some analysis devices also have a lightweight approach: processing Netflow instead of raw packets. Routers or switches are able to generate Netflow but the performance downgrade is inevitable. The better alternative is to let GRISM generate Netflow v5/v9 by aggregating and analyzing the span traffic from those routers or switches while span is not a heavy burden. Besides Netflow, GRISM is able to generate the application log for HTTP requests.
An out-of- band monitoring infrastructure
Software-defined Monitoring
GRISM xUDN provides a XML script interface to fully control GRISM. Comparing to APIs library, XML script is much easier for implementation with little learning overhead.
Monitoring Network Virtualization
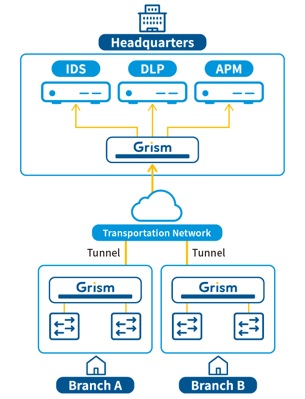
Centralized security analysis pool
To centralize the analysis resources such as network security devices, we can create the tunnel between two GRISMs so that monitoring traffic, mirror span, from different offices can be aggregated to the single site, the tunnel receiver, through IP network. GRISM support the proprietary X-tunnel and ERSPAN to carry the span traffic to form a many-to-one topology. The tunnel receiver unwraps the tunnel traffic and distinguish the sender by tunnel ID.
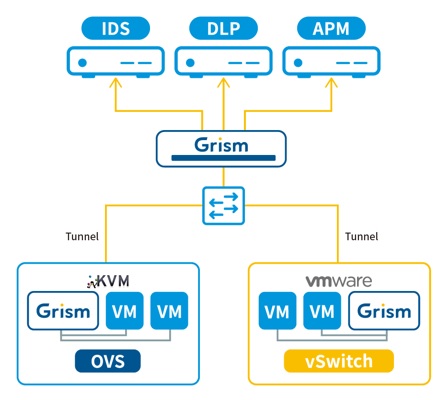
VM Traffic Monitoring
VM Traffic Monitoring
GRISM can direct the traffic inside the virtualization environment to those analysis resources which have been in physical networks.