Any-to-Any Delivery
- Each interface can be INPUT or OUTPUT
- 1-to-many, many-to-1, many-to-many
- To any selected interface after filtering
Advanced Distribution
- Filter Processor
- Composed of a set of rules with AND / OR operation
- Session-based filtering and packet-based filtering
- L2-L4 header filtering rule: MAC address, Ethertype, VLAN ID, IP range, TCP/UDP port…
- DPI-enabled Filter Processor
- L4-L7 Pattern-based filtering
- Pattern format: HEX, ASCII strings and Regular Expression
- Tunnel-awareness filter
- Apply all filtering rules on in-tunnel packets where GRE / VxLAN / QinQ / MPLS
- unnel ID (ERSPAN/X-tunnel) filtering
- Processor Chain
- User-defined graphs of Filter Processors
Out-of-band Load balance
- Same Dst IP / Src IP / Dst Port / Src Port sticky to same egress ports
- Same 5-tuple hash sticky to same egress ports
- Delivery HA: Re-distribute to link-up egress ports
- Balance port groups: Max 8 egress ports
Packet Engineering
- Tag removal: MPLS / VLAN / QinQ…
- Unpacking Tunnel (Tag removal and re-encapsulation): GRE / GTP / ERSPAN / NvGRE / VxLAN
- User-defined VLAN tagging for input packets or output packets
- Packet Deduplication
Monitoring Network Virtualization
- GRISM to GRISM tunnel
- Encapsulation: GRE, VxLAN, ERSPAN, X-tunnel
Network Traffic Intelligence Extraction
- Generate Netflow V5 / V9
- Generate HTTP log
- Generate DNS log
Front-line Security
- Massive Blocking
- IP / Domain / URL
- Max 2,000,000 entries
- 3rd party threat intelligence import
Sensitive Data Protection
- Packet slicing
- Preserve N bytes
- Remove TCP / UDP payload
- Data mask
- Replace sensitive data segment in TCP / UDP payload
- Data segment can be defined in regular expression
In-Line Aggregation and Re-Distribution
- N network links X M monitoring links (N X M)
- In-line session-based load balance with HA strategy
- Intelligent content-based bypass
- IP address List
- User-defined pattern in regular expression
PCAP File Processing
- Stream snapshot in PCAP format
- Filter PCAP files with timestamp persistance
- Remote recording agent over L2-L4 switch
Telecom Correlation Processing
- Mobile 3G / LTE data netwok
- Filter GTP-C / GTP-U by IMSI/IMEI
- Subscriber-based load balance
- Fixed ISP network
- Filter user-plane packets by RADIUS ID
- subscriber-based load balance
Virtual Machine Traffic
- VM traffic redirection by GRISM-V (as a VM instance)
- Supporting environment
- KVM
- VMware ESXi / vSphere
System Control and Operation
- Web GUI agent for authenticated users
- Advanced Control
- XML script over HTTP
- Management protocol: Telnet, HTTP, SNMP V2
|
GRISM G8
|
GRISM T4G
|
GRISM T12
|
GRISM T20
|
GRISM F2T12
|
GRISM AF6H48
|
GRISM AH32
|
|
|---|---|---|---|---|---|---|---|
| Network Interface | 1G RJ45*8 | 10/1G SFP+*4 | 10/1G SFP+*12 | 10/1G SFP+*12 |
40G*2
10/1G SFP+*12 |
100/40G*6
10/1G*48 |
100/40G*32 |
| Hardware Bypass | RJ45 port pair *1 | External | External | External | External | External | External |
| System Operation | HTTPS, SNMP v2/v3, GRISM XML script | ||||||
| Data Format | Ethernet/PCAP | Ethernet | Ethernet | Ethernet | Ethernet | Ethernet | Ethernet |
| Advanced Processing | 4Gbps | 10Gbps | 40Gbps | 90Gbps | 90Gbps | ||
| Forwarding and Replication | 8Gbps | 40Gbps | 120Gbps | 200GBps | 200GBps | 1.6TB | 1.6TB |
| IoC (IP/ Domain/ URL) Capacity | Max 1M | Max 2M | Max 5M | Max 10M | Max 10M | ||
| Power Supply Unit | AC 110V-220V | Dual DC -48V | Dual AC 110V-220V | Dual AC 110V-220V | Dual AC 110V-220V | Dual AC 110V-220V | Dual AC 110V-220V |
Key Functions

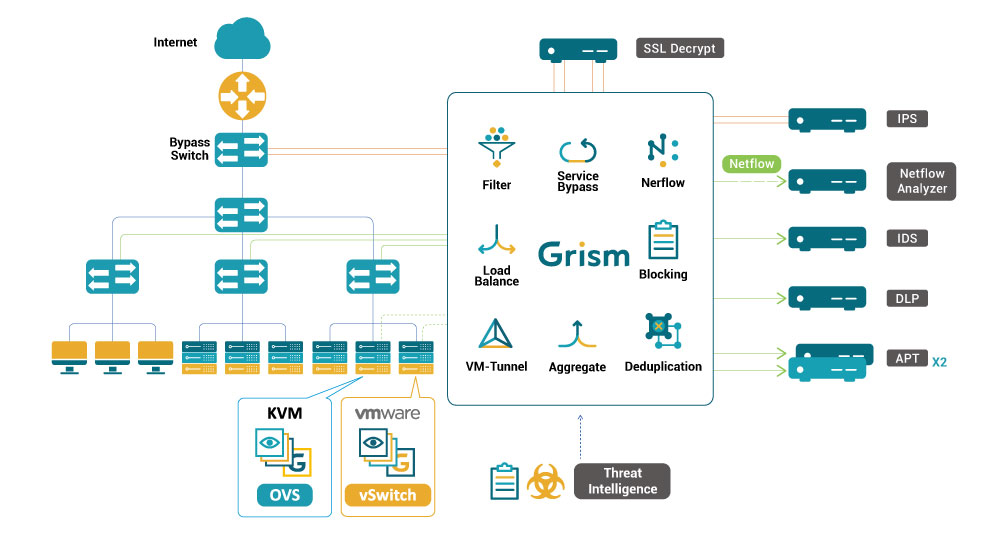
Netflow
Extract the network metadata from packet streams.

Service Bypass
Make the low-risk traffic skip security inspection.

Deduplication
Remove L3-above duplicated packets.

Filter
n-line or OOB session-based traffic load balance with HA configuration.

Load Balance
Collect traffic from several sources or interfaces.

Aggregate
L2 to L7 session-based or packet-based filtering.

Massive Blocking
Detect and block sessions by a massive list of IPs/Domains.

Tunnel
Tunnel for traffic span to support cross-site or VM2VM monitoring.

Packet Slicing
Removing specific section from packet.






